What is dllhost.exe and Why is it Running?

Windows has many processes running in the background. This time we’ll take a look at dllhost.exe to cover its functions and risks.
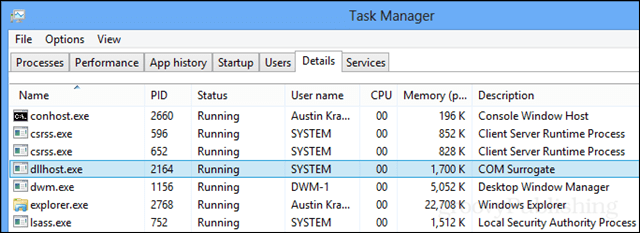
A quick peruse through Task Manager on any Windows system will reveal a process known as dllhost.exe running in the background. If you’ve found that, you’d probably like to know what it and its description of “COM Surrogate” are doing and whether or not it’s a safe process to have running on your computer. The good thing to consider is that it is supposed to be there. This is a process created by Microsoft and is packaged in every version of the Windows operating system.

There is a small chance that dllhost.exe could get infected by a virus. However, if your computer is up to date with all of the latest security patches from Windows Update and you have an anti-virus installed such as Microsoft Security Essentials then it’s highly unlikely that you’ll have any problems with infection.
What is COM+?
To understand what dllhost.exe does, you need to understand what the COM+ Service is. COM+ is short for Component Object Model. When pulling up the process/service in Process Explorer it doesn’t reveal much. The description for the process reads:
Manages the configuration and tracking of Component Object Model (COM)+-based components. If the service is stopped, most COM+-based components will not function properly. If this service is disabled, any services that explicitly depend on it will fail to start.
To really delve into what the process does we’ll have to take a look at the Microsoft Dev Center library. And it reveals that COM+ is primarily useful for the following:
- Deploying enterprise-level applications for an entire network.
- Providing pre-existing components for application development because COM+ is considered an object-oriented programming architecture.
- Running an event registry that handles system requests, enhances security, triggering process handles, and creating service request queues for applications.
COM+ consists of building block components that are self-defining and play well with others. The usefulness in this comes from the design of components being shared and reused by multiple applications. Not only does this design lower the demand for system resources, but it also improves initialization speed. The components object models are not written in any specific programming language, however, there are separate classes for each one depending on the programming language intended. On the enterprise level, this provides the advantage of mass deployment with a GUI tool Microsoft created called DCOM.
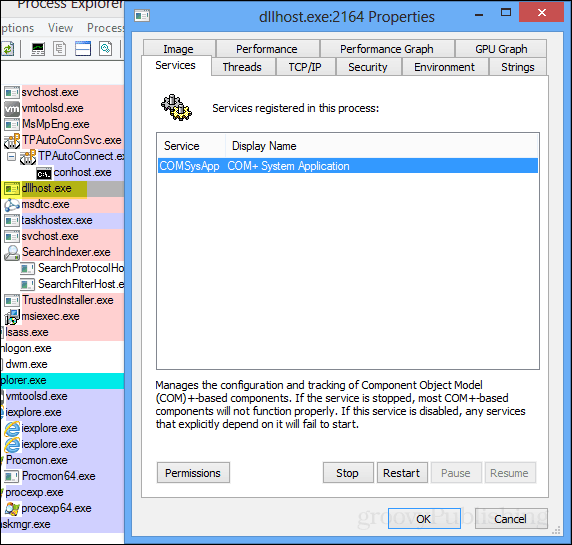

Dllhost.exe is a host for DLL files and binary executables.
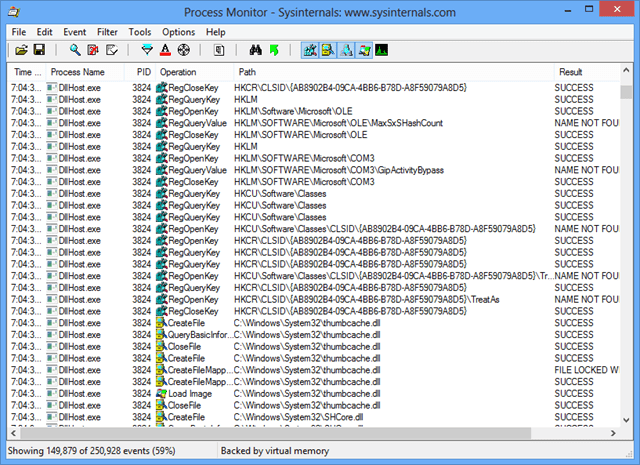
A DLL (dynamic link library) is essentially a size-unspecific block of code stored in a single file. This code can be the makeup of an application, service, or just an add-on for a graphical user interface. Dllhost.exe, similar to svchost.exe, is a required Windows service for any COM+ oriented programming code. A sample of what dllhost.exe runs is shown below using Process Monitor, which includes both .dll and .exe file types.
Risks
Dllhost.exe is typically safe as long as the computer is up to date on all security patches and a reliable antivirus is installed. If you see it in the following places you are safe:
- The official directory location for this process is C:\Windows\System32\dllhost.exe
- Dllhst3g is also a valid Windows process stored in the same System32 folder.
If dllhost.exe appears anywhere else, it is likely a virus. Some worm viruses mimic the name of dllhost and store themselves in the System32 folder. Here are a few examples:
- Worm/Loveelet-Y stores itself in /Windows/System32/ as dllhost.com
- Worm/Loveelet-DR stores itself in /Windows/System32/ as dllhost.dll
High CPU usage
One possible security flaw in the design of the COM+ system is that it allows any DLL stored on the system to run, assuming that the trigger initiating it the required permissions. This means that when you see a high CPU usage for dllhost.exe it is probably not the host process causing the problem, but rather a loaded DLL running through the host. You can use a program such as Process Explorer to investigate further.


Summary
Dllhost.exe is a safe Windows process created by Microsoft. It is used for launching other applications and services. It should be left running as it is critical to several system resources.
References:
4 Comments
Leave a Reply
Leave a Reply






wheelsey_4
September 4, 2013 at 11:04 am
That’s all great information, Austin. Thanks for the info. On a similar note, I think, I’m getting this RegSvr32 error message right when my laptop starts:
The module.
“C:\Users\CaptainClint\AppData\Local\….\jp2iexp.dll”
failed to load.
Make sure the binary is stored at the specified path or debug it to check for problems with the binary or dependent .DLL files.
The specified module could not be found.
wheelsey_4
September 4, 2013 at 11:06 am
I sure could use a little help, please.
Tom
September 13, 2014 at 3:40 pm
This is a better description of what dllhost is. However as helpful as you think you are you fell short of the answer. You mention dllhost getting infected. It doesn’t. There may be a bad file named the same. And if you delete it, it will reappear.
Can you write a panic about discovering the nit that is the actual Trojan? That would cover much more than just this one problem which is really a symptom.
Robert Sefton
June 16, 2020 at 3:17 pm
If this file does become Defective, could it be replaced with an operational version? If so, where could someone find this operational file? If not, what could be done to open created word documents and other apps?