Warning: Expired Domains Are Easy-Pickings for Hackers

Here’s a valuable lesson about not letting your domain registrations lapse without winding down all the other associated services. Don’t let this happen.
I learned a hard lesson this week. Long story short, a spammer from Vietnam has hijacked my Google Apps for Domains (now called Google Apps for Business) account and is currently sending people emails from my old email address (jack@anthrocopy.com) complete with my signature, phone number and name, and everything on it. Anthrocopy.com was an informal dba name I used years ago for my freelance writing business, but I slowly phased it out and let the domain expire. Now, someone else has moved into the place, hermit-crab style, and are probably contacting all my old business contacts about cheap Viagra.
I contacted Google about it and their official response was “I’m sorry to tell you that we cannot assist you with this problem since you don’t own that domain anymore.”
Fair enough. After all, I let the domain expire, thereby letting someone else buy it, and in doing so, I let them commandeer my old Gmail account, Google Docs account, and any other third-party web service I may have used Google authentication to log into. Google tech support recommended I contact law enforcement, but I think the FBI has bigger fish to fry than some Vietnamese spammer pretending to be a mild-mannered freelance writer.
So, it seems as the only recourse left for me was to spread the word that I’d been hijacked and, in the process, perhaps provide a public service announcement about letting your domain registrations lapse without winding down all the other associated services. The details of those two efforts follow.
Why Am I Getting Failed Delivery Notifications for Emails I Didn’t Send?
I’m not sure why this happened to me, but lately, I’ve been getting a lot of failed delivery notifications or out-of-office auto-replies for emails that I never sent. One of these emails is what tipped me off to the fact that something ungood was happening to my online identity.
Email Spoofing vs. Compromised Email Account
The first few I received were a simple case of email spoofing. That is, someone was sending emails saying that they were from me, but the headers of the email proved that they really weren’t being sent from my account. Email spoofing is a common, often automated attack, and is mostly harmless since most mail servers know how to recognize a spoofed email. SPF records can help this effort.
Here’s an example of a simple spoofed email:
Delivery has failed to these recipients or groups:
teddy-metsseuk@gammoninsurance.com<mailto:teddy-metsseuk@gammoninsurance.com>
The e-mail address you entered couldn’t be found. Please check the recipient’s e-mail address and try to resend the message. If the problem continues, please contact your helpdesk.
Diagnostic information for administrators:
Generating server: higginbotham.net
teddy-metsseuk@gammoninsurance.com
#550 5.1.1 RESOLVER.ADR.RecipNotFound; not found ##
Original message headers:
Received: from ecsdel01.appriver.com (72.32.253.39) by mail.higginbotham.net
(10.5.2.56) with Microsoft SMTP Server id 14.1.218.12; Tue, 29 Apr 2014
00:41:57 -0500
Received: from [10.238.8.145] (HELO inbound.appriver.com) by
ecsdel01.appriver.com (CommuniGate Pro SMTP 5.3.12) with ESMTP id 401638471
for teddy-metsseuk@gammoninsurance.com; Tue, 29 Apr 2014 00:41:58 -0500
X-Note-AR-ScanTimeLocal: 4/29/2014 12:41:56 AM
X-Policy: higginbotham.net
X-Primary: teddy-metsseuk@higginbotham.net
X-Note: This Email was scanned by AppRiver SecureTide
X-Virus-Scan: V-
X-Note-SnifferID: 100
X-GBUdb-Analysis: 0, 97.67.222.18, Ugly c=0.425302 p=0.483871 Source Normal
X-Signature-Violations: 100-5950968-462-494-m
100-5948747-463-494-m
100-5946619-2051-2065-m
100-5946619-7869-7883-m
100-5946619-9947-9961-m
100-5946619-11129-11143-m
100-5950968-0-11316-f
X-Note-419: 0 ms. Fail:0 Chk:1342 of 1342 total
X-Note: SCH-CT/SI:0-1342/SG:1 4/29/2014 12:41:55 AM
X-Warn: BOUNCETRACKER Bounce User Tracking Found
X-Warn: OPTOUT
X-Warn: REVDNS No Reverse DNS record for 97.67.222.18
X-Warn: HELOBOGUS HELO command issued with no domain.
X-Warn: BULKMAILER
X-Warn: WEIGHT10
X-Warn: WEIGHT15
X-Note: Spam Tests Failed: BOUNCETRACKER, OPTOUT, REVDNS, HELOBOGUS, BULKMAILER, WEIGHT10, WEIGHT15
X-Country-Path: UNITED STATES->UNITED STATES
X-Note-Sending-IP: 97.67.222.18
X-Note-Reverse-DNS:
X-Note-Return-Path: teddy-metsseuk@anthrocopy.com
X-Note: User Rule Hits:
X-Note: Global Rule Hits: G327 G328 G329 G330 G332 G337 G384 G405 G417 G419 G427 G437 G438 G479
X-Note: Encrypt Rule Hits:
X-Note: Mail Class: VALID
X-Note: Headers Injected
Received: from [97.67.222.18] (HELO [97.67.222.18]) by inbound.appriver.com
(CommuniGate Pro SMTP 5.4.1) with ESMTP id 191929257 for
teddy-metsseuk@gammoninsurance.com; Tue, 29 Apr 2014 00:41:56 -0500
From: DrOZNetwork Newsletter <teddy-metsseuk@anthrocopy.com>
To: <teddy-metsseuk@gammoninsurance.com>
Subject: You Will Lose At Least a Size Every Fortnight
Date: Tue, 29 Apr 2014 01:41:57 -0400
List-Unsubscribe: <mailto:leave-b3db3c9506b063bce889d7-978be4013ce282fcd5d6-256aab091be3e6c64a2c8-a86f159b1d43a9b5f2-b4b398@leave.e.gammoninsurance.com>
MIME-Version: 1.0
Reply-To: “DrOZNetwork Newsletter” <reply-teddy-metsseuk@anthrocopy.com>
x-job: 00645_45748849
Message-ID: <a0c7833a-67bb-cf14-f329-40a11eb37c6a@gammoninsurance.com.local>
Content-Type: multipart/alternative; boundary=”MeDnwMAYvTCJ=_?:”
Return-Path: teddy-metsseuk@anthrocopy.com
But then, I received a failed delivery notification that included the original message. And I noticed that it had an actual email address that I once used (jack@anthrocopy.com) and my email signature, too. This was evidence that not only was someone saying they were me, but they were also actually sending legitimate emails out from my old address. It was actually sent via Gmail.


How could this be? It seemed that my old Google Apps for Domains account had the credentials for my still active main email address in it. Not good.
First, I was worried that a computer that I had recently given to a friend was being abused. But I looked up the IP address (1.54.46.59) from the sender’s header, and it appeared that the email was sent from someone in Vietnam. I checked my StatCounter log and also found that the hacker had been visiting my webpage:


It seems that someone is specifically and persistently trying to steal my identity. I have no idea why. But by stealing Anthrocopy.com from me and my associated Google Apps for Domains account, it seems like they’ve made some progress.
How Hackers Can Access Your Gmail by Buying an Expired Domain
Google Apps for Domains is different from a normal Gmail or Google Docs or Google Drive account in that it is associated with a domain that you may have registered from a company other than Google. Back in 2010, I registered Anthrocopy.com with Namecheap.com. After I wound down my freelance career to work as a full-time technical writer, I let the domain expire. Somehow, the hacker found out that I had a Google Apps for Domain account, even though I no longer owned the domain. So, on June 20, 2014, somebody bought it through moniker.com, according to Whois.
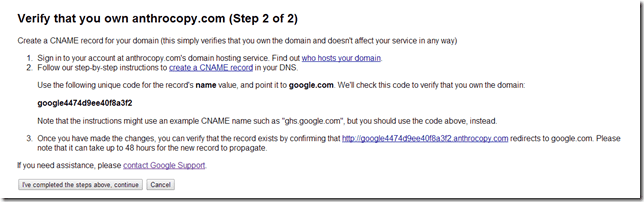

That’s fair game. If I don’t want a domain name anymore, someone else is free to buy it. However, they took it a step further and hacked into my Google Apps for Domains account. They did this by using the Google Apps for Business account recovery form, which will give you access to any Google Apps account if you can prove that you own a domain name. Instead of using a password reset or password hint, you can just create a CNAME record for the domain that proves that you own the domain. Then, Google gives you the keys to the account. For $10, someone in Vietnam has just gained access to all of my old Gmail settings, history, and saved login credentials.
Recovering a Hijacked Google Apps for Business Account
Spoiler alert: there’s no way to recover a compromised Google Apps for Business account. If someone owns the domain, they own the associated Google Apps for Business account. That’s Google’s position on it, and I highly disagree, but I haven’t convinced them to do anything about it yet.
When I learned what had happened, I contacted Google Enterprise Support via this form. About 12 hours later (on a Saturday, not bad), I received a call from a friendly fellow who recapped my incident accurately. Unfortunately, he told me that there was nothing I could do if I could not prove that I owned the domain. I told him that I didn’t care about the domain, I just wanted my personal and professional information and credentials out of the hands of that random person. The tech said he’d escalate the situation, but shortly afterward, I received the following email:
Hello Jack,
Thank you for answering my call. I understand that you were the owner of ‘anthrocopy.com’ and created a Google Apps account using that domain but you didn’t renew it so someone else registered and took control of your Google Apps account.
As per our conversation, in order to have a Google Apps account you need to own the domain you’re tying to use. Another person took control of the domain since she/he was able to prove ownership via DNS settings. I’ve consulted this case and I’m sorry to tell you that we cannot assist you with this problem since you don’t own that domain anymore. As a provider of content creation tools and hosting services, Google is not in a position to mediate or adjudicate disputes between third parties. We recommend that you raise your concerns directly with the administrator in question.
If you believe that the administrator in question is unlawfully restricting access to your account, we recommend that you contact law enforcement.
Sincerely,
Guillermo.
Google Enterprise Support.
So, at this point, I’m stuck.
What Am I Going to Do About My Online Reputation?
My next step is to send out a personal email to everyone I can think of that may be in that contact list. And perhaps post a notification on the websites for the domains that I do still control. But other than that, it looks like there isn’t much I can do, other than to go public with what happened and try to apologize and explain to each person affected. I hope to win the PR battle by making it widely known that Anthrocopy.com and jack@anthrocopy.com are bogus and that the real Jack Busch is very upset and very sorry.
Learn from My Mistakes: Don’t Let Domains Lapse
I used to buy domains like crazy whenever Godaddy had a 99 cent domain name sale or I thought of a funny idea for a website. Now, I realize that each one of those is somewhat of a liability. Each one that I own and then disown becomes an avenue for someone to co-opt my identity. With Anthrocopy, which was the only one I registered a Google Apps account with, that domain that I bought four years ago and let expire turned into a huge vulnerability.
The wider lesson from this is to never let old accounts lapse or expire. Keep tabs on every account you create online. If you decide to stop using the account, delete it. Don’t trust the service provider to trash your data once it’s no longer useful to you. Whether it’s an old Twitter account, an old Facebook account (read our article on how to permanently delete your Facebook account), an old Xanga blog, or even an old AOL account, dig it up now and delete it, or at least scrub it from any personal information. On the web, it’s finders keepers, and what you lose will be too small of potatoes for law enforcement to get involved.
Recommendation to Google
While I appreciate how quickly a Google representative reached out to me, I’m disappointed that there isn’t any further recourse. It’s one thing to buy up a property that someone has abandoned. It’s another thing to be able to buy up that property and then assume their identity afterward. I realize that I should have been more vigilant about my old, inactive accounts, but I feel like it’d be a productive policy to have an expiration date on inactive accounts as well. I registered Anthrocopy four years ago and stopped using it completely over two years ago. I think at that point, it wouldn’t be annoying for Google to send me a quick email: “Hey, you still using this? If not, we’ll delete it.”
I think this should be the policy for anything. Twitter, Facebook, MySpace, Gmail, etc. There should be an administrative purging of data for abandoned accounts. This policy should be upfront in the terms of service and, perhaps, you could give the option to disable automatic deletion of inactive accounts.
I imagine that attacks like these are going on right now and will continue to occur until we all wise up and delete old accounts (fat chance) or service providers start implementing measures to prevent zombie accounts from coming back and eating the brains of our former colleagues with spam (or worse).
Conclusion
I made a mistake and I learned my lesson. I’m doing my best to perform damage control and prevent this from happening again. But if you’ve had a similar experience or have further insight or suggestions, I’d love to know.
10 Comments
Leave a Reply
Leave a Reply





TomP
July 1, 2014 at 10:59 am
This is really really bad. I have about a dozen domains I let expire and a few were hosted at google apps…
Now I know what I’m doing today!
Thanks Jack.
TP
Raymond
July 1, 2014 at 1:20 pm
Thank you for the excellent article Jack.
Joe
July 1, 2014 at 3:31 pm
Ok, it’s clear that the hacker fully owns your Google account now. What’s not clear is whether he is able to access other accounts of yours that rely on it. What I mean is if all he can do is access your contact list and send them spam, it’s not a very big deal. But if can obtain credentials you use elsewhere (banks and other important websites that are tied to that account), then you should contact a lawyer.
Jack Busch
July 6, 2014 at 11:08 am
I’m afraid that he can. Google allows you to authenticate third party accounts (Twitter, Pinterest, etc.) by being logged into a Google Apps account. This is my main concern. I’m continuing to harp on Google tech support. I hope I don’t have to lawyer up.
Norm
July 2, 2014 at 7:11 am
While the previous owner is at fault, Google shares much of that fault! If all a hacker needs to do is prove they own the domain name, then Google Apps for Business needs a better initial setup policy.
A phone number or something that can easily identify that person — granted you could lose that number, but most people don’t go through numbers like crazy. Something that would ask you to verify if you’re in a different IP address from where you normally would be. And if you don’t pass the authentication process, can prove you own the domain name, the old Google Apps gets deleted and replaced by a new Google Apps.
Google loves to create things for ease but never takes the time to realize the long-term consequences. Excite should have bought them when they had the chance…
Jack Busch
July 6, 2014 at 11:09 am
Funny thing is that I did have a phone number associated with the account. The hacker changed it so I can’t recover it using that number anymore. He moved in and changed the locks.
CMapley
July 4, 2014 at 2:32 am
To me this seems like a simple fix for google.
As part of the settings for the account there should be an option to disassociate it from the domain and record a reason for doing so.
Perhaps this option already exists and it is just the case that you didn’t realise that it NEEDED to be done.
Although no-one likes to be the subject of a cautionary tale, this has provided a valuable insight into a flaw in Google’s service and perhaps there are others out there who don’t even realise that there old account may well now be in the hands of someone else.
I would be disappointed if Google did nothing to rectify this in order to prevent future abuses, even if it may be too late in your own case.
Jack Busch
July 6, 2014 at 11:10 am
I agree with you, CMapley. In fact, I suggested that to Google Tech Support that there be a way to “reset” my account starting at the time that it “changed ownership” (if that’s what we are calling it). We’ll see what they say…
Des Donnelly
July 6, 2014 at 6:12 am
Hi Jack
it would be useful if you could share the case id (with me directly) for the exchange with Guillermo.
Regards
Des Donnelly
Jack Busch
July 6, 2014 at 11:06 am
Des – I can forward you the entire email chain. Ping me at jack@groovypost.com and I’ll send it to you.